It is now in the Instructions Menu.
Continue reading “Added New Page for Auto Update ipfilterX in Peerguardian Linux”
by Nexus23 Brotherhood

It is now in the Instructions Menu.
Continue reading “Added New Page for Auto Update ipfilterX in Peerguardian Linux”

Despite being around for so long, there is still some confusion among internet users about how Peerblock works.
#§§-§§§###############
#>ipfilterX_K3 Series:
#
#>Date:[15 June 2022]
#
#[UPDATE DETAILS]:
#
#Threats:
#_Blocked:[135]
#_Updated:M:[8]:AP2P[7]:S[3]:G:[3]
#_IP Added Record:[+5K]
#_Merged/Extended:[12]
#_Deleted:[14]
#_Level:[CRITICAL]
#
#COUNTRIES INVOLVED:
#[_JP-US-UA-UK-CZ-SK-CN-TW-PL-NL-FR-IT-BR-AU-CA-DE_]
#


#Little Snitch used also by Hacking Team for their purposes
###########
At last Peerguardian for MAC is still working :
https://sourceforge.net/projects/peerguardian/
SNAPSHOTS PEERGUARDIAN MAC OSX:
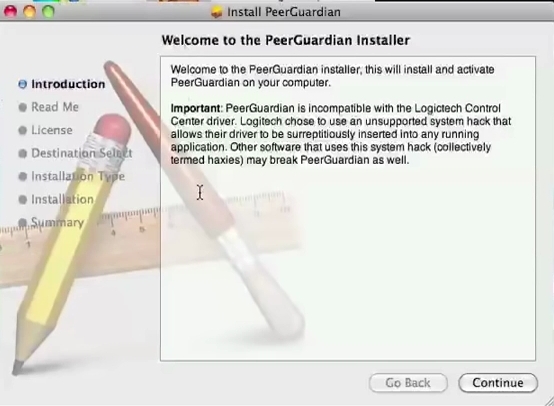
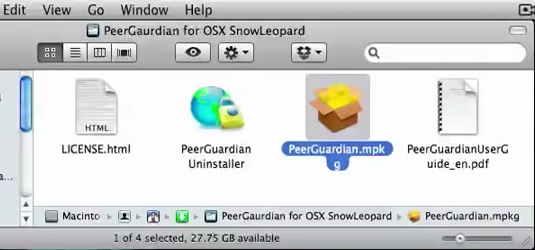
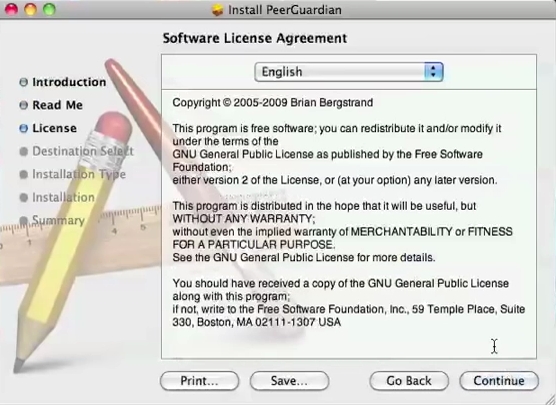
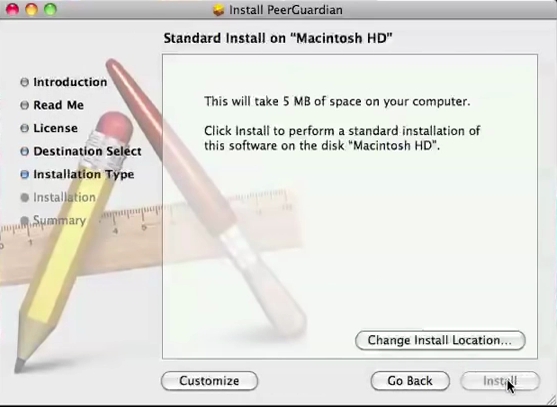
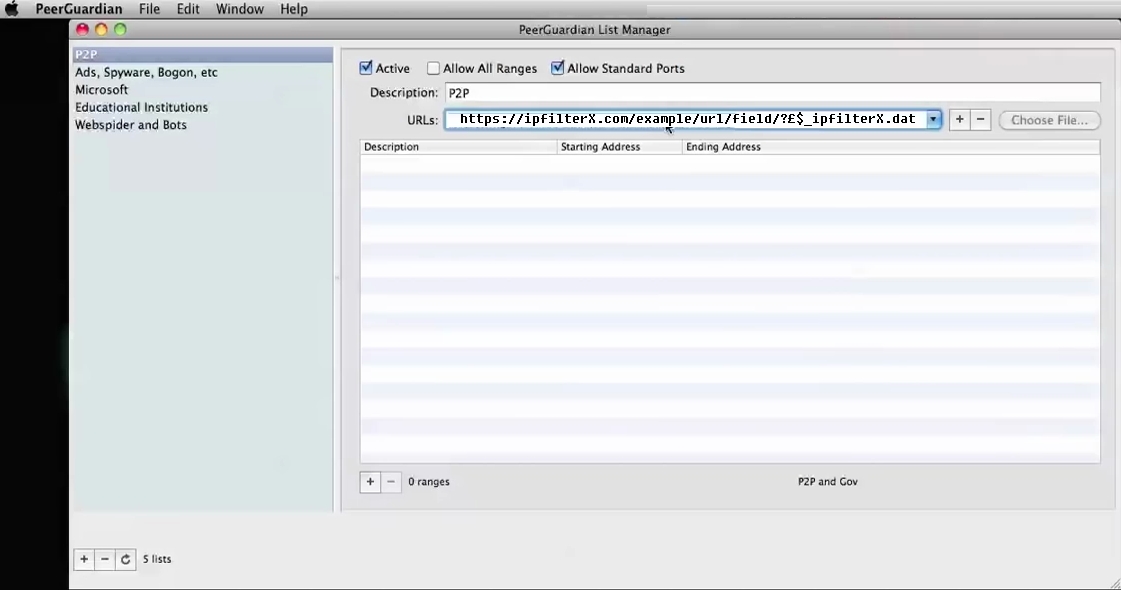
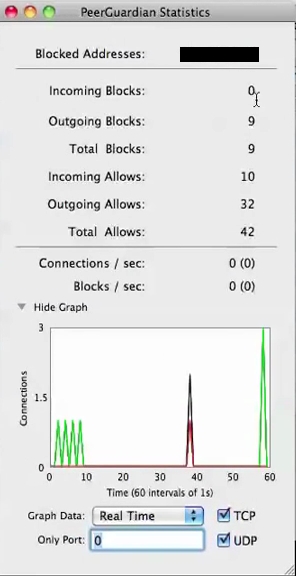
###################
OTHER
See IPFW Rule , option to import rules.
LITTLESNITCH
Also Littlesnitch got a rule like that –
Rules can cover a list of multiple hostnames, domains or arbitrary IP address ranges, helping you to simplify your ruleset.
ICEFLOOR
Positive comments on
Icefloor is a current alternative to the outdated (yet still functionable) PeerGuardian if you are using OS X.
It is a frontend for the pf firewall/packet filter, which is meant replace ipfw (which PG uses) in newer versions of OS X.
The programmer of Icefloor is working on a new software that also supports OS x 10.10 and superior.
However, in Icefloor, ip lists can only be loaded from files, not via the web.
http://www.techrepublic.com/article/configure-apples-built-in-network-firewall-with-icefloor/
FIGURE L and FIGURE O
A similar grid exists for listing connections established by applications, connected hosts, or sockets actively listening for communications. Grid lists information for each connection made by an app, protocol, source, and target IPs, plus the ports they’re connected to/from, and current status (Figure O). For additional security, you can terminate connections at will from the list or ban IP addresses to prevent future connections from taking place.
Figure P.
Such information, available at a glance, includes packet loss bandwidth — both incoming and outgoing. Whitelisted or blacklisted IPs, with relevant details in transmission rates for those connections, is also included. Lastly, the Network Services List button details many common and not so common services for both UNIX and OS X. This information is quite helpful when troubleshooting an issue with a rule that needs to be modified due to incorrect port assignments or to prevent clashing with another offered service
MURUS FIREWALL:
http://murusfirewall.com/
They own an option to import blacklists
-T command [address …]
Specify the command (may be abbreviated) to apply to the table. Commands include:
-T kill Kill a table.
-T flush Flush all addresses of a table.
-T add Add one or more addresses in a table. Automatically create a nonexisting table.
-T delete Delete one or more addresses from a table.
-T expire number
Delete addresses which had their statistics cleared more than number seconds ago.
For entries which have never had their statistics cleared, number refers to the
time they were added to the table.
-T replace Replace the addresses of the table. Automatically create a nonexisting table.
-T show Show the content (addresses) of a table.
-T test Test if the given addresses match a table.
-T zero Clear all the statistics of a table.
-T load Load only the table definitions from pf.conf(5). This is used in conjunction
with the -f flag, as in:
Here another way :
Create a file called :
/Library/Server/Mail/Config/postfix/client_access
Add your IPs to client_access in the following format:
123.123.123.123 REJECT
Add as many single IPs or IP blocks as needed.
Save and issue:
sudo /Applications/Server.app/Contents/ServerRoot/usr/sbin/postmap /Library/Server/Mail/Config/postfix/client_access
Edit
/Library/Server/Mail/Config/postfix/main.cf
and add:
check_client_access hash:/Library/Server/Mail/Config/postfix/client_access
to the parameters present in smtpd_client_restrictions
For example:
smtpd_client_restrictions = permit_mynetworks permit_sasl_authenticated check_client_access hash:/Library/Server/Mail/Config/postfix/client_access reject_rbl_client zen.spamhaus.org reject_rhsbl_client dbl.spamhaus.org permit
When done, issue:
sudo /Applications/Server.app/Contents/ServerRoot/usr/sbin/postfix reload
See also here: http://www.postfix.org/postconf.5.html#check_client_access
Regarding Postfix Paths in Server 5, see here: https://topicdesk.com/faqs/why-do-postconf-n-and-postfix-reload-produce-unexpect ed-output-on-os-x-server-5/
################

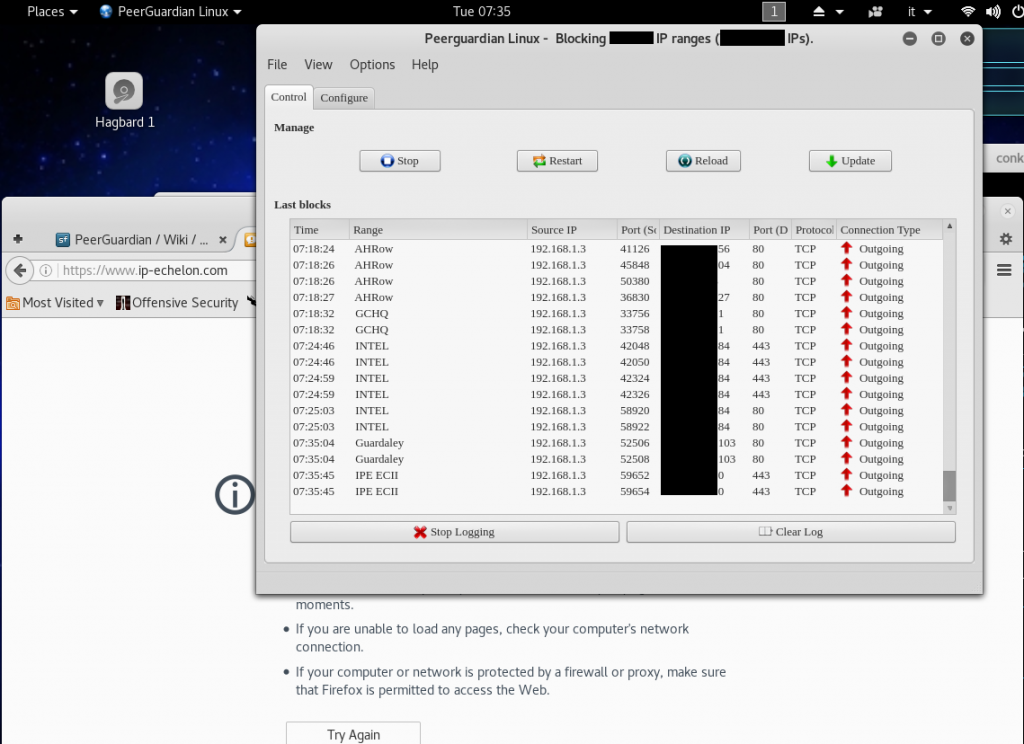
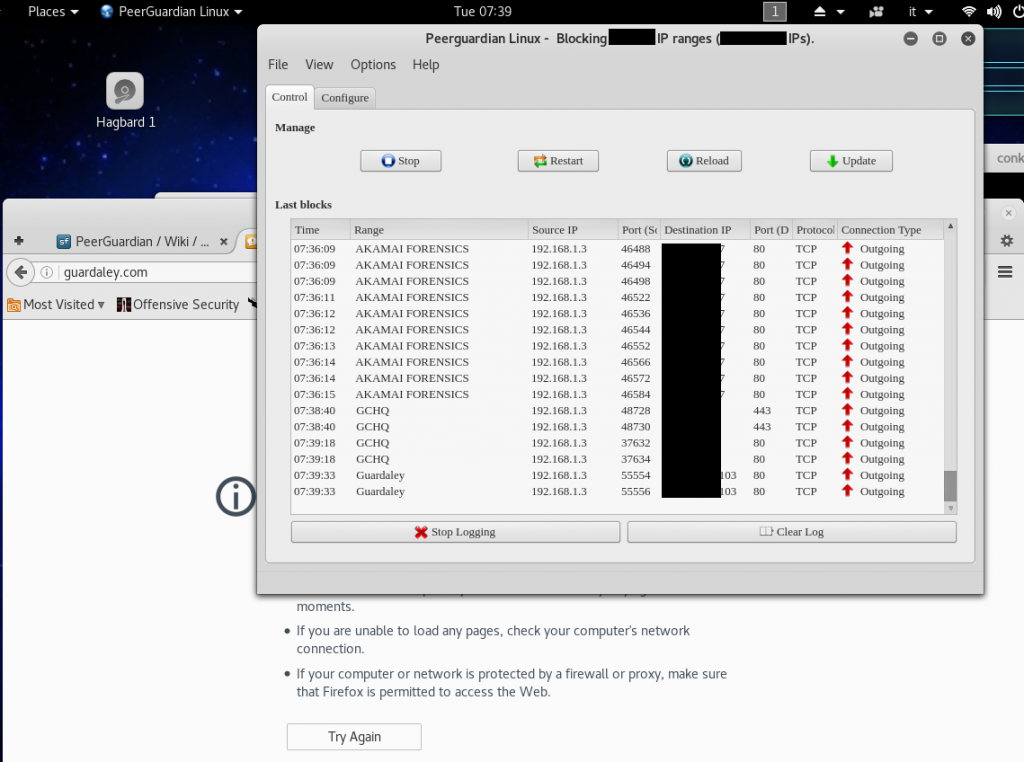
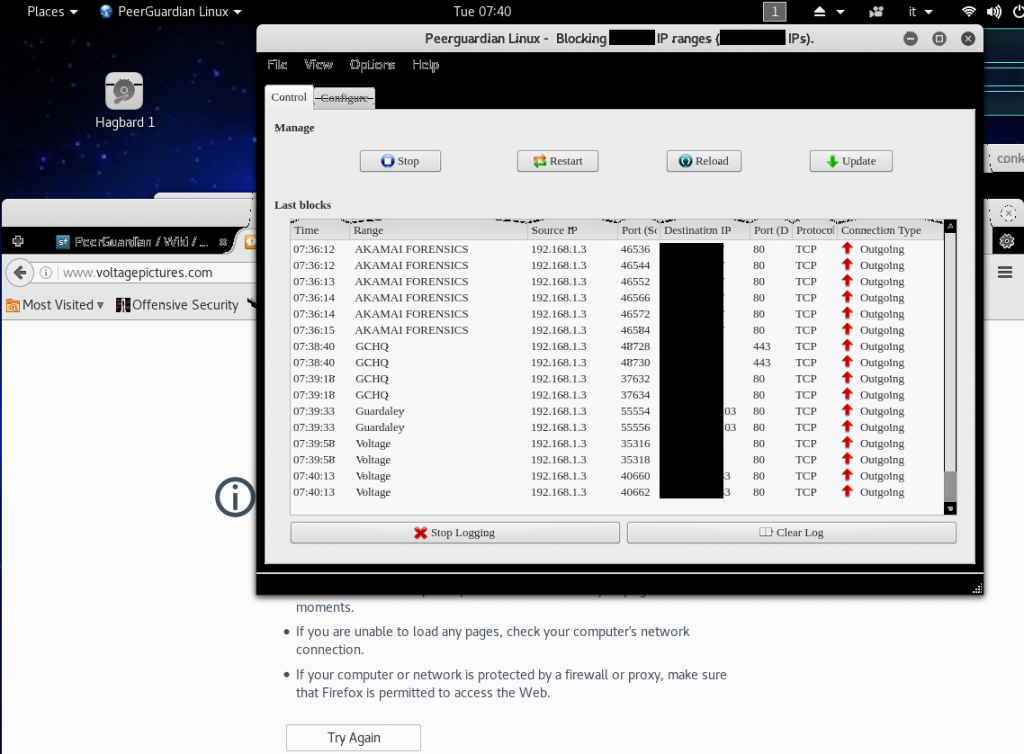
#Peerguardian and MoBlock Debian
In the specific Peerguardian Linux works as well. It loads also .dat file extension for e2dk.
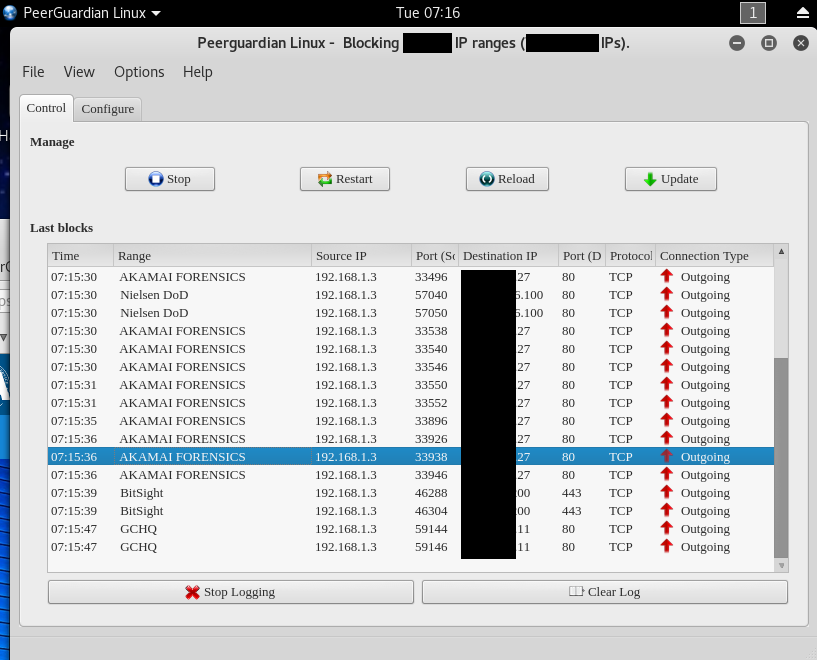
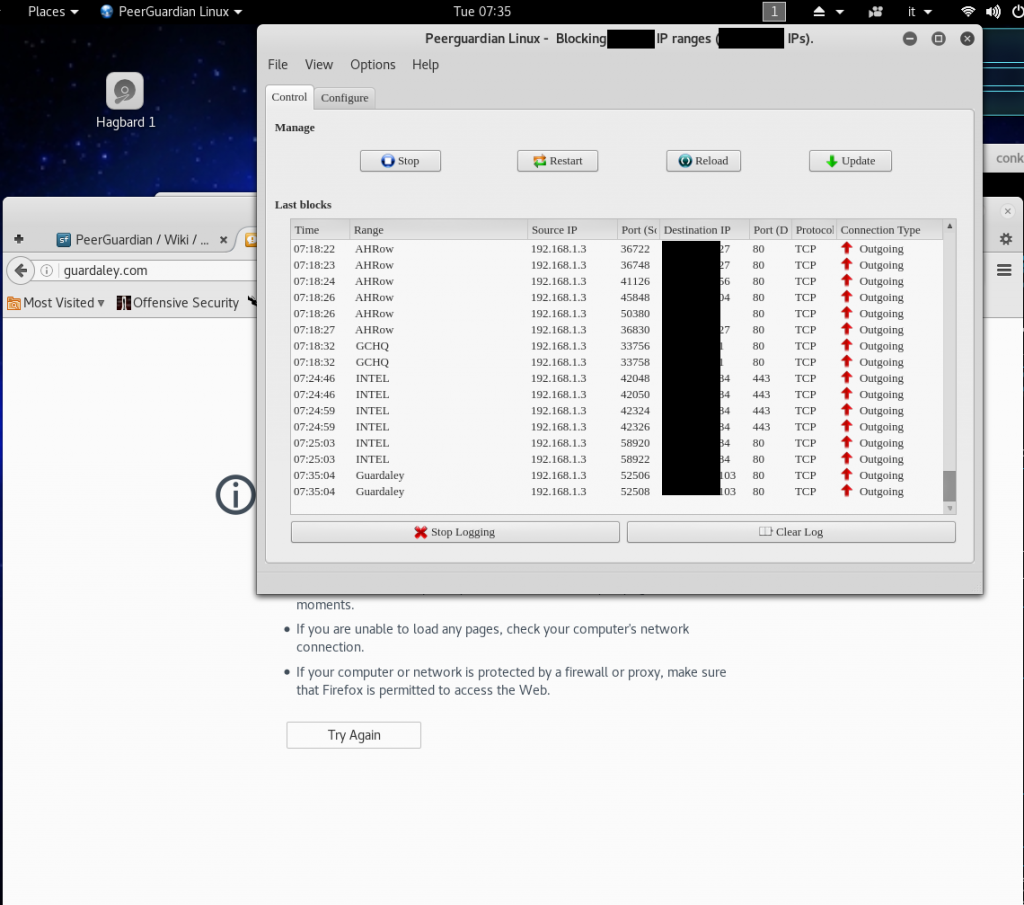
SSL URLs for ipfilterX update work like a charm.
Tested it in Kali Linux latest release 2016.2 with no problem at all.
Here some screenshot
,,,òmòm